"Modernize Managed IT Security Governance & Service"
Emerging threats, risks and new technologies are creating the uncertainty to business. BROCENT as managed IT security service provider help clients manage enterprise security functions and free up your security staff to focus on overall program oversight.
IT SUPPORT & SECURITY GOVERNANCE
IT Security Service Offering
- Detection, monitoring, investigation and management of threats (security events generated, parsed, triggered, or observed from BROCENT managed technologies)
- Monitoring and alerting of the system health of all managed technologies
- Technology support including updates/upgrades, and software optimization
- Technology specific services such as Firewall rule changes, tuning, and repair support
- Dedicated technical expertise for device management requests such as moves/adds/changes, additional investigations, and service tuning
- Threat Advisory research communications
- Regular operational reporting through the HG Portal, visualized dashboards, and automated monthly reports
IT Security Service Coverage in ASIA
BROCENT operates the Security Control Center in Asia to deliver the proven IT security solution to customers with local premise offices and manufacture plants , and enhance local IT security management by implementing the IT solution solutions as SOC, that covers, BCP, Antivirus, Data Backup, Network Security, System Security and so on. The ISO 27001 and CISSP certified consultant works to assess and audit the IT environment and provides the IT assessment report and remediation plan in China, Singapore, Tokyo, Vietnam.
IT Security Director- JIE, ZHANG
PREVENTIVE IT SECURITY CHECK
For most SMB customers, the topic of IT Security Management is closely related to the plan of IT routine support. It touches the fundamental concepts whether the very basic IT security measures are implemented, and whether the plan of routine IT system check is in place. This section illustrates the mandatory tasks from preventive support plan , that shall be considered and scheduled on weekly and monthly basis. That does not take too much time indeed, but will make your IT system more solid.
Daily/Weekly Security Matters

Antivirus &Anti-Malware
Check the antivirus management console the overall status, particularly to identify if there be any infected devices, outdated antivirus definition.

Data Backup & Recovery Drill
Check the system log and backup outcome from the management console, particularly to identify if there any major failure of backup event. And take remediation to resume if it is

System Availability Management
Check the critical infrastructure and system's availability, covering the windows server, Linux application, network device and the power supply devices and so on.
Monthly Security Matters

Gap analysis for antivirus clients
Review the list of antivirus clients and identify further if there be any outdate client or missing client.

Review the Server Security Patches
Use ATERA and WSUS to manage all pending security patches, and manage to install the patches in the maintenance window

Account and Password
Review the AD and email user account list to identify if there is any invalid user account e.g. resigned employee
Quarterly Security Matters

Physical Server Health Check
Review the server and storage’s status by remote support so as to identify those changes on system configuration and alert.

Core Device’s configuration backup
Examine the backup configuration and the execution plan, and store them into the configuration database

Firmware Upgrade
Cross check with manufacture and see if there is any critical firmware upgrade and enforce the upgrade plan
RESPONSE OF IT SECURITY INCIDENTS

IT Security Incidents happen on every single second. Capture the security event and respond immediate to take remediation action. BROCENT IT security NOC service is standby 24 x 7 for your hassle free on IT security management
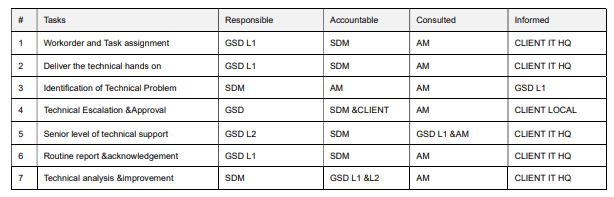
MANAGED SECURITY SERVICES WORKFLOW

Incident Alert
Security Incident management system is to receive all your alerts for BROCENT NOC process and justification

Analyze Incident
After the technical analysis, NOC will advise client if any critical IT asset is impacted, and advise the action plan

Acknowledge/Fix
Most useless alert will be ignored and acknowledged, while the technical measures will be in place to correct them.

Remediate Risk
After the technical actions, a remediation plan will be in place to prevent the similar risk from routine operation.
IT Assessment and Remediation Plan

IT ASSESSMENT & AUDIT
BROCENT Consultants make using the IT automation and Risk analysis tools to run the IT assessment and Audit report with the proper remediation Plan with the Budget.

IT Assessment Report
BROCENT Security specialist uses the qualified assessment tools to collect the information of IT Asset, configuration &settings and visualize the assessment gap analysis to identify the risk and business impacts.
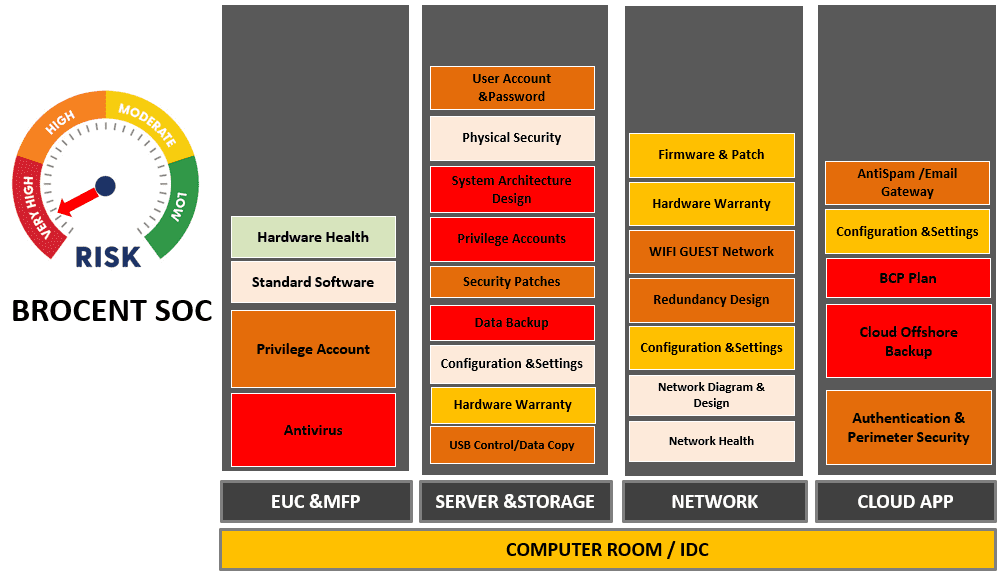
A practical IT Security management for SME IT to address the major risk and hassle free IT solution of keeping business data integrity and continuity.
Prioritizing the Findings & Risk
Fundamental security weakness , that impacts the business data integrity and continuity, are considered as critical risk, in consideration of the business impact level and IT budget, an itemized risk categorization and priority shall be presented to customers as the basis reference of IT remediation action plan.
Remediation & Action Plan
A concrete risk remediation plan to determine further the cost of OPEX, and the cost of CAPEX investment for customer senior management to determine how the plan shall be implemented stage by stage. OPEX is about the IT professional service to correct the IT configuration risk, while CAPEX is to invest extra infrastructure or cloud service to fill the IT Risk gap.
