Change in Demand
The IT architecture and security situation changed, and the internal threat index increased
Various information security threats follow
Brocent can provide SANGFOR Network Behavior Management AC
Network behavior management supports the visual and controllability of terminals, applications, data and traffic on the entire network, intelligently senses internal risks such as terminal access violations, Internet violation behaviors, and sensitive data leakage, and realizes terminal access control, Internet access control, and data leakage control Integrated behavioral safety control.
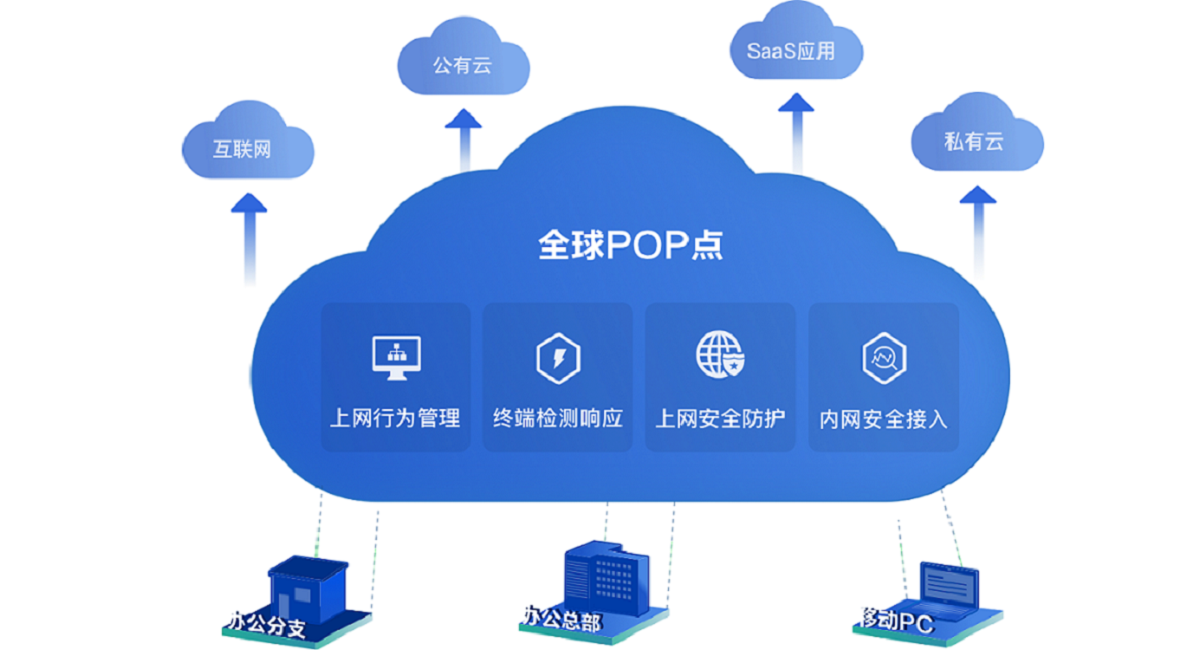
Product function introduction
BROCENT also can provide Cisco Umbrella services
Cisco Umbrella provides secure access to the internet and usage of cloud apps everywhere

Get to know the new Cisco Umbrella
Integrated cloud security service benefits

Flexible security protection on and off network

Consistent policies across remote locations

Better performance and user satisfaction everywhere
Multiple security functions in a single cloud security service
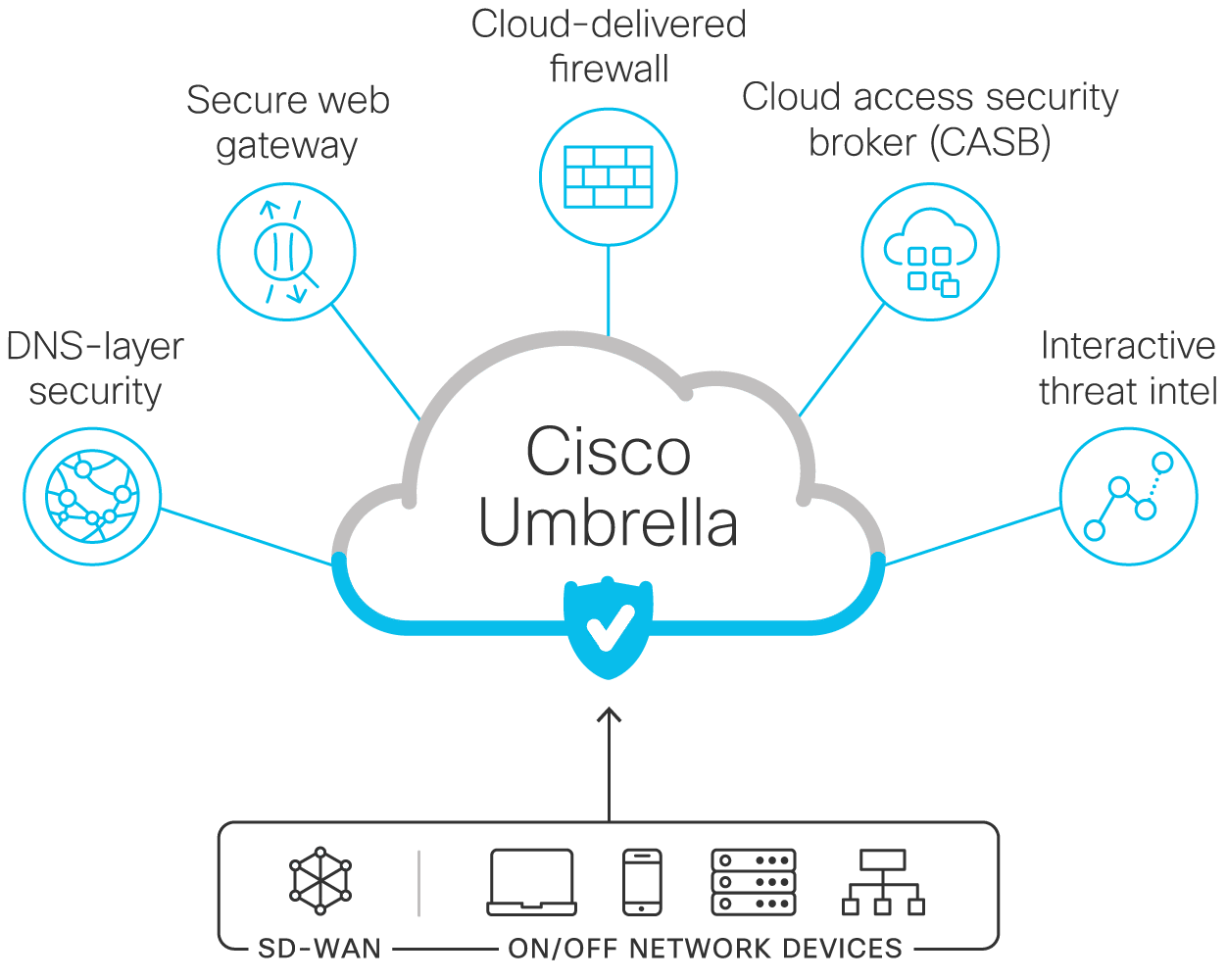
Cisco Umbrella’s security functions

DNS-layer security
Umbrella’s DNS-layer security provides the fastest, easiest way to improve your security. It helps improve security visibility, detect compromised systems, and protect your users on and off the network by stopping threats over any port or protocol before they reach your network or endpoints.

Secure web gateway
Umbrella’s secure web gateway logs and inspects web traffic for full visibility, URL and application controls, and protection against malware.
Use IPsec tunnels, PAC files, or proxy chaining to forward traffic to our cloud-based proxy to enforce acceptable use policies and block advanced threats.

Firewall
Umbrella’s firewall logs all activity and blocks unwanted traffic using IP, port, and protocol rules. To forward traffic, simply configure an IPsec tunnel from any network device. As new tunnels are created, policies are automatically applied for easy setup and consistent enforcement everywhere.

Cloud access security broker
Umbrella exposes shadow IT by providing the ability to detect and report on cloud applications in use across your organization. For discovered apps, view details on the risk level and block or control usage to better manage cloud adoption and reduce risk.

Interactive threat intelligence
Our unique view of the internet gives us unprecedented insight into malicious domains, IPs, and URLs. Available via a console and API, Umbrella Investigate provides real-time context on malware, phishing, botnets, trojans and other threats enabling faster incident investigation and response.

Integration with SD‑WAN
The Umbrella and Cisco SD‑WAN integration deploys easily across your network for powerful cloud security and protection against internet threats. Our integrated approach secures cloud access and efficiently protects your branch users, connected devices, and app usage from all direct internet access breakouts.
A secure fit for all businesses

Umbrella improves performance to SaaS apps by up to 33%
Our cloud security service advantage

Unmatched intelligence
Powered by Cisco Talos, one of the world’s largest commercial threat teams, Umbrella blocks malicious activity earlier, before it reaches your network or endpoints. Umbrella also uses statistical and machine learning models to uncover new attacks staged on the internet.

Reliable infrastructure
Highly resilient cloud infrastructure with 100% business uptime since inception in 2006. With carrier-neutral data centers globally, Umbrella delivers superior speed by peering with over 1,000 of the world’s top internet service providers.

Easy API integration
Umbrella offers APIs to more easily deploy and share intelligence and security event details with your security systems and workflows. Get more out of your existing investments and speed up incident response.

Feel free to contact us Brocent




