WHY NEED MANAGED ENDPOINT SECUIRTY?
Office computers, employee BYOD devices, and company-owned mobile devices. All functionality is supported within a single MDM management console that manages user accounts, passwords, permissions, authorized applications, etc. They all need to managed endpoint protection
All company owned IT asset e.g., computer and mobile devices are distributed and used by employee. MDM supports to manage the security throughout the whole life cycle. Data will removed remotely to protect company if that is lost.
Employees come and go without incurring additional costs, as the MDM solution is pay-as-you-go. The entire security solution can be used in all work scenarios, including home offices, training centers and office computers. It's a very convenient managed endpoint protection solutions
ENFORCE IT POLICY TO ENDPOINTS
Client IT infrastructure tends to be light weight and cloud based. There is less chance to invest local on-premise server with Active Directory and Group Policy for ECU computer and mobile device management. Moving to the best option of mobile device management makes much technical flexibility of IT infrastructure design and meanwhile comes with strengthened EUC IT management, and no compromise with Managed Endpoint Security. No heavy IT software investment. Pay as your business Grows.
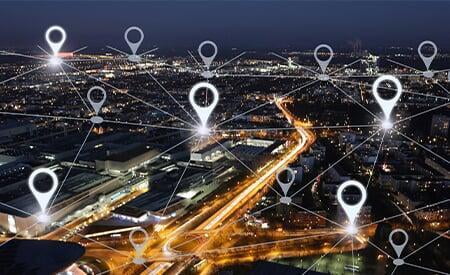
Geofencing – Location based MDM restriction
Geofence functionality, in the context of an MDM, let’s the administrator define policy zones and policy-exclusion zones. Policies with admin-specified restrictions and profiles are automatically configured on to devices that enter the geofence. Geofencing is ideal for field devices that house business-sensitive data and are constantly in different locations. MDM allows creation of multiple geofences all around the world.

Managed Endpoint Data Security and Encryption
Perform full disk encryption on Windows 10 PCs using BitLocker, Microsoft’s built-in tool for encrypting system drives, data drives and removable data drives. BitLocker encrypts the entire Windows operating system, offering protection against unauthorized access of a lost or stolen Windows device.
Seamlessly separate corporate apps and data from personal apps and data by deploying “containers” on devices.
Perform seamless disc encryption on Mac devices using Apple’s full disc encryption program “FileVault” to prevent unauthorized users from retrieving the information store on Mac. Once the device is encrypted, anyone without a password or recovery key will be unable to log in to your Mac.

Application Security
Restrict access to Google Play Store, iTunes Store, Apple’s App Store, Microsoft Store Apps, iBooks, podcasts, to prevent users from installing non-productive apps on corporate devices. Prevent managed app data from syncing with your iCloud account. This prevents devices from syncing corporate data with its iCloud account.
Deploy proactive internet access controls to monitor the bandwidth usage of apps on devices. Configure per-app VPN on to establish secure access to corporate data from managed device endpoints.
Add value to your business
SECURITY GOVERNANCE OF DATA, DEVICE AND APPS.
The end security solution supports Windows 10, Mac, Android, and Iphone
Password Policy
Data Encryption
Web content Filter
Enterprise Apps
Remote Grant Access
Remote Data Wipe
Withdraw Access
Remote Lockdown
MDM Technologies
In the business case, BROCENT uses the combination of Technologies to achieve the business expectation of security management and flexibility.
The Technologies cover the MDM, centralized authentication, cloud infrastructure, monitoring and security audit.




Device Theft Prevention

DLP &Threat Management

