Protect Organization Data against Adrozek
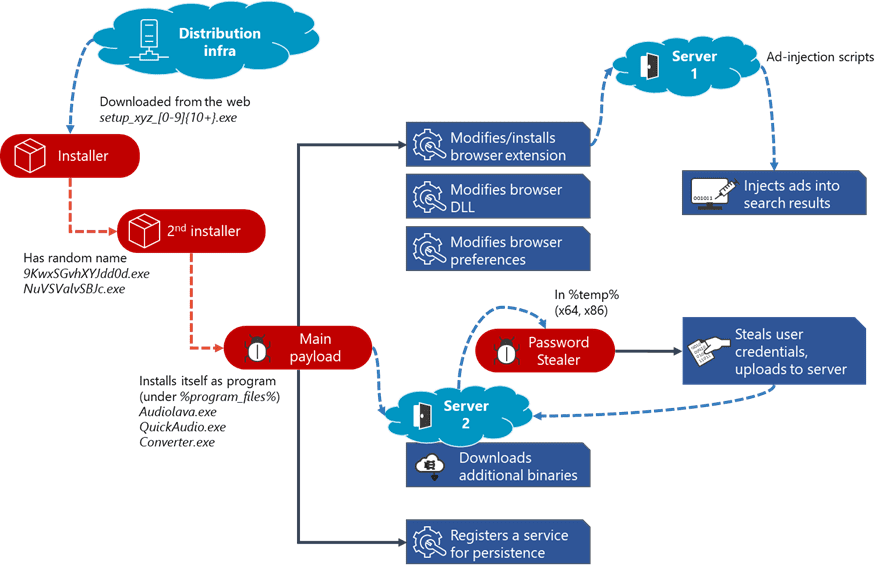
Adrozek is a malicious browser modifier that, when installed on users’ machines, infects them with adware. This particular strain of malware has been making rounds since May 2020; according to Microsoft, it was at its peak in August, when as many as 30,000 computers were affected per day. Although classified as adware, Adrozek is also designed to collect information extracted from browsers by modifying browser settings and extensions. It affects Google Chrome, Microsoft Edge, Mozilla Firefox, and the Yandex browser. Considering the risks Adrozek poses to organizations, IT admins need to take some preemptive measures to ensure security.
How does Adrozek affect your organization?
Adrozek is being distributed through drive-by attacks, where users are tricked into installing the malicious software, often bundled with or disguised as legitimate software. Once installed, it makes a number of modifications to browser settings and extensions. Adrozek disables browser updates and turns off Safe Browsing, which is a feature designed to prevent users from landing on malicious websites. It then installs and activates new browser extensions that run in incognito mode; these extensions run without explicit user permissions, and are hard to notice since they aren’t displayed in the toolbar. These modifications help the malware inject users’ search engines with ads. In certain browsers, the malware further steals users’ credentials. When users access enterprise web applications on the infected browsers, the organization’s data security is at risk.
How to protect your organization against Adrozek
It’s always better to be safe than sorry. IT admins can implement a stringent yet foolproof, three-step preventive mechanism to help secure their organizations against Adrozek.
1. Restrict users’ access to trusted websites
Implement URL filtering software to prevent users from accessing websites that are unauthorized by the IT teams. This ensures that users don’t land on infected websites, preventing the installation of malware.
2. Limit downloads to trusted websites
While step one eliminates the chances of users installing the malware, limiting downloads to trusted websites creates an additional layer of security, preventing it from being downloaded in the first place.
3. Restrict execution of untrusted applications
Restricting the execution of untrusted applications will prevent Adrozek from running if it’s present in the enterprise network. This final step creates a fortified boundary, preventing the execution of the malware.
BROCENT Managed IT Security Service (MSS) to implement these three-fold preventive measures. In case users’ machines are already infected with Adrozek, IT admins can implement a few best practices to limit the damage.
1. Deploy browser configurations to users’ browsers
Browser configurations and behavior can be managed from a central location with the managed antivirus console. Configurations deployed cannot be overwritten by users, nor by Adrozek. For example, deploying a configuration to enable browser updates will prevent the malware from modifying the setting. Similarly, BROCENT support center can enable the Safe Browsing configuration, ensuring that Adrozek cannot disable it. This will minimize the impact of the malware.
2. Restrict installation of new browser extension and add-ons
IT admins can restrict the installation of new extensions and add-ons. This will prevent the malware from installing new extensions capable of injecting ads and stealing credentials. To prevent loss of productivity that could arise from lack of extensions, mission-critical extensions and add-ons can be distributed to users’ browsers BROCENT managed network behavior management console.