SECURITY MATTERS FOR BUSINESS EMAIL
Implement and Enforce IT Security Tools to have a legacy email from external attack and data compromise from Anti-Spam, Anti-Virus, Email Content Encryption, Delegation and Approval, and Contingency Plan from Unexpected failure. BROCENT managed email security solution delivers the cost efficient solution, that is Pay as you Go
Managed Email Security
Email security uses technology to inspect incoming emails for malicious threats and encrypt--or secure--outbound email traffic to protect mailboxes, data, users, and organizations from cybersecurity attacks and schemes. Cloud email security is increasingly important as more and more companies migrate to a cloud or hybrid email platform. Cisco Email Security's layered defenses can provide comprehensive protection that incorporates email security best practices .
CONCERNS ON EMAIL SECURITY &GOVERNANCE
How Email Security Works
Email accounts can be compromised by attackers using phishing attacks or otherwise, exposing your email communications to cyber criminals. Email messages and attachments can also be intercepted as they travel over the email network. By default, emails are not encrypted as they travel from your emails servers to the recipient. This means that if hackers are able to compromise this data, they can read your emails and attachments.
When emails are encrypted however, the contents of the emails are scrambled, so that only the intended recipient can access them. Make sure that encryption works, that is important, and the easiest ways for organizations to implement email encryption.
Ramsomeware and The Business Impact
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid.
In many cases, the victim must pay the cybercriminal within a set amount of time or risk losing access forever. And since malware attacks are often deployed by cyberthieves, paying the ransom doesn’t ensure access will be restored.
Ransomware holds your personal files hostage, keeping you from your documents, photos, and financial information. Those files are still on your computer, but the malware has encrypted your device, making the data stored on your computer or mobile device inaccessible.
- Crypto malware. This form of ransomware can cause a lot of damage because it encrypts things like your files, folders, and hard-drives. One of the most familiar examples is the destructive 2017 WannaCry ransomware attack. It targeted thousands of computer systems around the world that were running Windows OS and spread itself within corporate networks globally. Victims were asked to pay ransom in Bitcoin to retrieve their data.
- Lockers. Locker-ransomware is known for infecting your operating system to completely lock you out of your computer or devices, making it impossible to access any of your files or applications. This type of ransomware is most often Android-based.
- Scareware. Scareware is fake software that acts like an antivirus or a cleaning tool. Scareware often claims to have found issues on your computer, demanding money to resolve the problems. Some types of scareware lock your computer. Others flood your screen with annoying alerts and pop-up messages.
- Doxware. Commonly referred to as leakware or extortionware, doxware threatens to publish your stolen information online if you don’t pay the ransom. As more people store sensitive files and personal photos on their computers, it’s understandable that some people panic and pay the ransom when their files have been hijacked.
- RaaS. Otherwise known as “Ransomware as a service,” RaaS is a type of malware hosted anonymously by a hacker. These cybercriminals handle everything from distributing the ransomware and collecting payments to managing decryptors — software that restores data access — in exchange for their cut of the ransom.
- Mac ransomware. Mac operating systems were infiltrated by their first ransomware in 2016. Known as KeRanger, this malicious software infected Apple user systems through an app called Transmission, which was able to encrypt its victims’ files after being launched.
- Ransomware on mobile devices. Ransomware began infiltrating mobile devices on a larger scale in 2014. What happens? Mobile ransomware often is delivered via a malicious app, which leaves a message on your device that says it has been locked due to illegal activity.
Source from MIMECAST
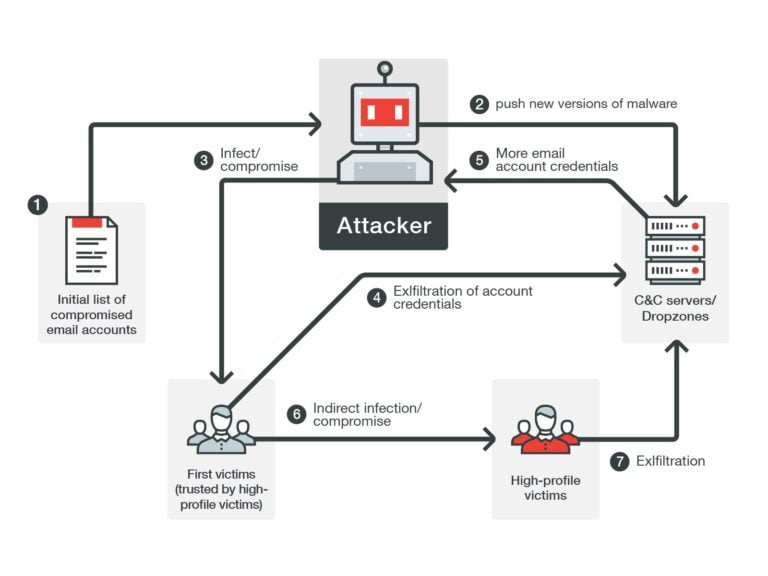
Prevent Email Compromise Internally
Internal email threats can result from a compromised email account, a malicious employee or the unintended consequence of human error. And, no single email security control is 100% effective. Therefore, it is essential that internal emails are continuously monitored to detect threats that the gateway cannot detect, such as email account takeover, and new threats discovered post-delivery. Email security service is deployed inside your email perimeter to detect, contain and automatically remediate threats, and your protection from internal cyber threats is completed.
MAIN FEATURES OF MANAGED EMAIL SECURITY
Data Encryption
Offers a number of encryption features. It is fully integrated with a cloud-based email encryption service for outbound email. Email that matches policy or is marked for encryption via the Outlook Add-in is sent securely via TLS to the Message Center, that uses AES with 256-bit keys to encrypt email.
The data encryption solution can be setup to on-premise solution and cloud based email system
Spam and Virus Pre-filtering
The Email Security Gateway is integrated with a cloud-based service that pre-filters email before delivery to the onsite Email Security Gateway. The Cloud Protection Layer is continuously updated with definitions in real time. The Cloud Protection Layer ensures that an organization’s email security infrastructure scales with the increasing growth in email volume, attachment sizes, and the organization as a whole.
Spam Protection
The Email Security Gateway leverages to identify email from known spammers and determine whether domains embedded in email lead to known spam or malware domains. Its industry-leading techniques protect against attempts to embed text inside images with the intent of hiding content from traditional spam filters.
Advanced Threat Protection
Advanced Threat Protection (ATP) combines behavioral, heuristic, and sandboxing technologies to protect against zero hour and targeted attacks. ATP automatically scans email attachments in real-time; suspicious attachments are detonated in a sandbox environment to observe behavior. In addition to blocking the attachment, the results are integrated into the Real Time Intelligence System providing protection for all other customers.
Outbound Email Security
Email is a critical vehicle in today’s business world, therefore a failure of the email server can significantly limit business operations. With the Cloud Protection Layer, bundled free of charge with the Barracuda Email Security Gateway, email is spooled for up to 96 hours, with an option to re-direct traffic to a secondary server.
Outbound Email Filtering
Outbound filtering prevents organizations from being put on spam block lists and prevents sensitive email data from leaving the organization. Employees can inadvertently cause internal systems to become a source for botnet spam. By using a subset of its defense layers, the Email Security Gateway’s outbound filtering stops outbound spam and viruses. It also lets administrators enforce content polices for data loss prevention (DLP) and meet other content standards in outgoing email.
Simplify email security
Simple and easy to deploy configurations on the Email Security Gateway guarantee that customized email protection is in place in a matter of minutes. Cloud-based centralized management enhances day-to-day workflow and is included with no additional fees.
Email Spooling
The Email Security Gateway ensures that email can still be delivered even during email server failures or loss of connectivity. In the event of on-premises disruptions, email can be spooled in the Cloud Protection Layer (CPL) for up to 96 hours. An alternate destination can also be specified if delivery to the primary destination fails.
During email server outages, the email for all mail servers is visible through the Cloud Protection Layer. From the message log, administrators can see the status of all spooled emails and whether email has been re-delivered
Stop threat before reaching the network
Offload CPU-intensive tasks like antivirus and DDoS filtering to the cloud reduces the processing load on the appliance and to ensure that threats never reach the network perimeter.
Enhance End User IT Security
- Email service plays unique and critical important role in business operation. More business are moving to Office 365 to have the enhanced email service experience. However, customer still worries about those virus, spam and other sorts of threats embedded in the email message, that irreversibly threats the business continuity.
- We also received the worse news from some new customers, they need professional IT service to address the Ransomware issue , and apparently it has encrypted all those files on the individual computer and the file servers. There is big chance that such threats come from USB, Email and internet surfing & download.
- With evolvement towards to the cloud computing era, the tradition IT infrastructure and security protection scheme is getting less efficient, that causes large proportion of mobile users' computer and business data exposed to the internet. And security issues can not be identified and addressed timely.
- BROCENT supports customer to design and implement the cloud based security architecture to protect End User and LAN users from complex security threats, that covers -
- Email security gateway to filter the email content and have critical business message encrypted;
- End user cloud antivirus to make user antivirus scanning engine and definition updated in compliance;
- URL control to safeguard end users' computer from malicious attack by visiting dangerous website;